Mi sitio web

Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


What Are The Benefits of Vulnerability Risk Assessment Solutions?
07 Nov 22 - 05:03
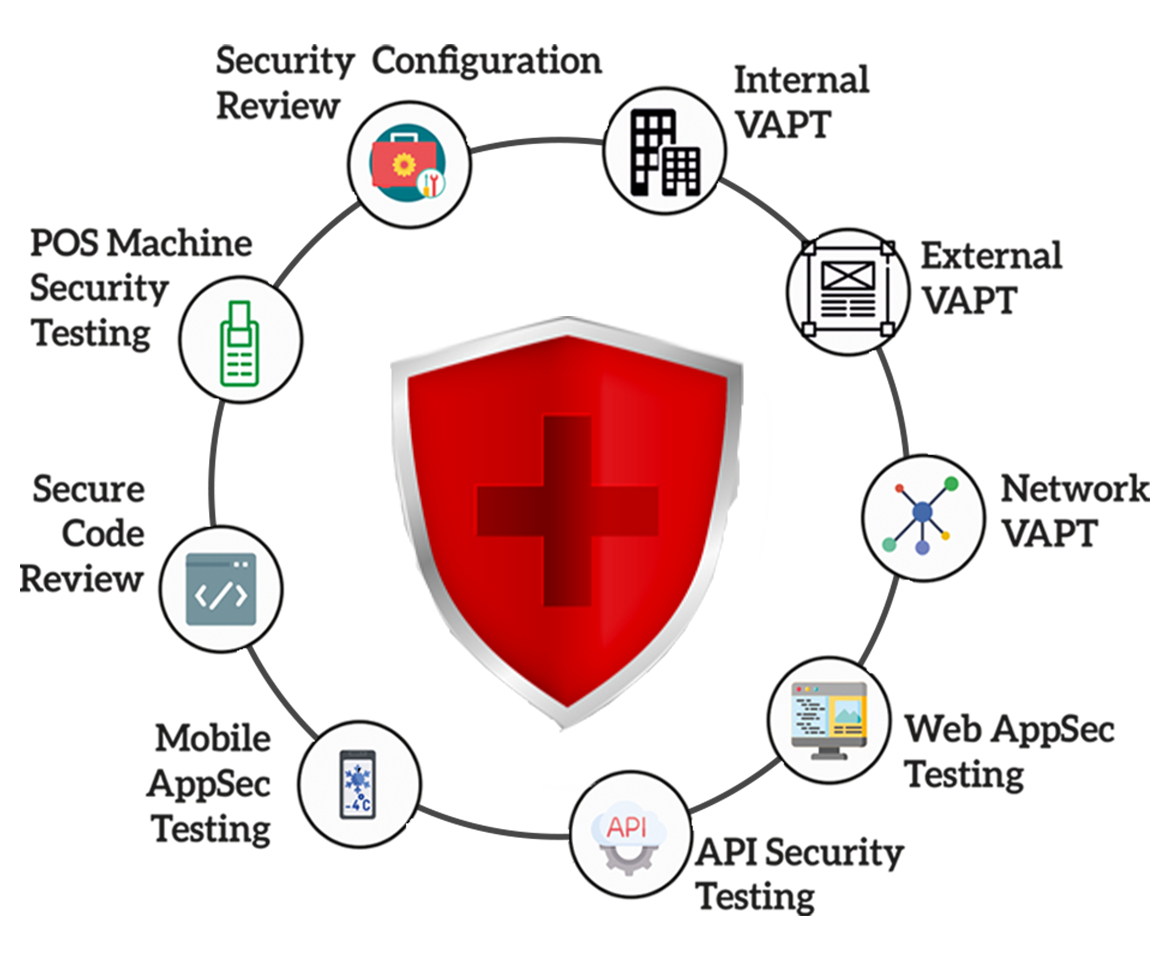
Vulnerability Risk Assessment Solutions
Companies are being hacked at an extraordinary speed across the world because of hackers exploiting software flaws. A vulnerability assessment is one of the most crucial tools you can use to defend your website. A vulnerability analysis detects software issues before they are exploited by hackers.
Hacking has become a lucrative business in and of itself. In the hacking industry, there are two primary models: the nation-state model and the private model. So it is essential to safeguard our sensitive data against hacking and breaches. A reliable vulnerability risk assessment solution is essential for this purpose.
How do hackers find your website?
Thousands of hackers are constantly scouring the internet for software security flaws. If you have any doubts about how extensive their attempts are, check any internet connection, whether at home or at work, and you will see hundreds of requests pinging a connection every day.
When they discover a system weakness, it is recorded in a database of comparable defects. When they uncover the desired amount of weaknesses, they either launch the assault or sell their findings on the dark web marketplace.
What exactly are software flaws?
Security gaps or application vulnerabilities can take several forms. It's either a software problem or a configuration issue that occurred during installation.
Vulnerability Analysis
A vulnerability assessment is vital weapon against hackers. The evaluation consists of three parts: inventory, security vulnerabilities scan, and feedback. A vulnerability evaluation is necessary to develop a strategy for identifying and fixing software vulnerabilities.
• Inventory
The first stage in an evaluation is the examination of the network to determine which equipment is connected to it. It may come as a surprise, yet there are frequently unaccounted-for devices on a network.
• The Vulnerability Assessment
The following stage is a scan to hunt for software bugs that meet the dozens of thousands of existing vendor flaws. When it identifies one, it logs it and continues.
A normal company with 100 people will have between 10 and 25 servers, as well as any number of switches, workstations, routers, and so on. A single scan can detect between 5,000 and 7,000 software weaknesses on the network at any given moment. These figures are staggering, but the good news is that not every one of these flaws constitutes an imminent threat.
A vulnerability analysis report can give an admin a set of vulnerabilities that can be handled right away. Assessments should be performed on a frequent basis to avoid hacker's attention. Every day, the aim should be to reduce risk and strengthen the company's security posture. This is only possible only through vulnerability risk assessments carried out and are handled on a consistent basis.
Tu Sitio Web Gratis
© 2025 Mi sitio web217502
Add a comment