Mi sitio web

Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


ISO 27001 Certification
17 Jan 23 - 01:29
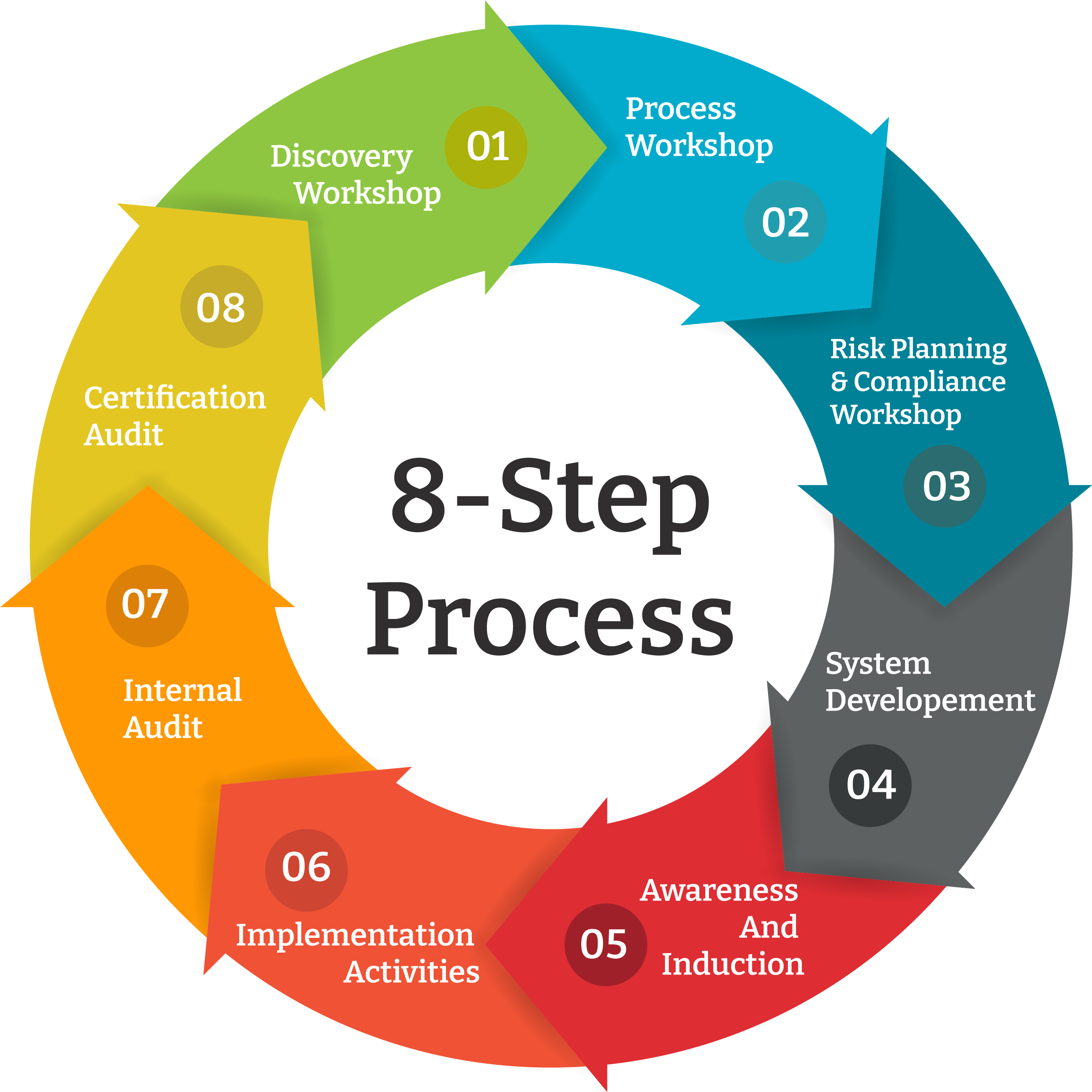
What Are The Standard Requirements to Get ISO 27001 Certification?
ISO 27001 Consultant
The ISO 27001 certification process typically involves an assessment by an accredited third-party auditor, who will review the organization's ISMS documentation and conduct on-site audits to verify compliance with the standard. The auditor will then issue a report detailing any non-conformities or areas for improvement, and the organization must address these before being awarded certification.
To achieve ISO 27001 certification, an organization must demonstrate that it has implemented a comprehensive information security management system (ISMS) that meets the requirements of the standard. This includes having policies, procedures, and controls in place to manage information security risks and to ensure the confidentiality, integrity, and availability of information.
The standard covers several key areas, including:
1. Security management: The organization must establish, implement, maintain, and continually improve an ISMS. This includes having a clear and documented information security policy and objectives, as well as assigning responsibilities for information security management.
2. Asset management: The organization must identify and classify its information assets and ensure that they are protected appropriately. This includes having controls in place to prevent unauthorized access, use, disclosure, disruption, modification, or destruction of the assets.
3. Access control: The organization must have controls in place to ensure that only authorized individuals have access to sensitive information. This includes having policies and procedures for granting and revoking access, as well as measures to prevent unauthorized access.
4. Cryptography: The organization must have controls in place to protect sensitive information during storage and transmission. This includes having policies and procedures for encrypting data and for key management.
5. Physical and environmental security: The organization must have controls in place to protect sensitive information from physical threats such as fire, floods, and theft. This includes having measures in place to protect the organization's premises, as well as its information processing and storage equipment.
6. Operations security: The organization must have controls in place to protect sensitive information during processing and transmission. This includes having policies and procedures for managing system and application vulnerabilities, as well as measures for ensuring the availability and integrity of the information.
7. Communication security: The organization must have controls in place to protect sensitive information during transmission. This includes having policies and procedures for protecting data in transit, as well as measures for ensuring the confidentiality and integrity of the information.
8. System acquisition, development and maintenance: The organization must have controls in place to ensure that the information security aspects of any new systems or applications are considered and managed. This includes having policies and procedures for managing the security of third-party systems and applications.
9. Incident management: The organization must have a defined incident management process in place to detect, report and respond to security incidents, including maintaining incident logs and reporting incidents to the appropriate authorities.
10. Business continuity management: The organization must have a defined process in place for ensuring continuity of its critical business operations, including maintaining business continuity plans and testing them regularly.
By implementing an ISMS that meets the requirements of the standard for ISO certification, organizations can gain a competitive advantage and can improve their reputation and credibility with customers, suppliers, and other stakeholders.
Tu Sitio Web Gratis
© 2025 Mi sitio web216409
Add a comment